This tutorial will cover a scenario where there are two local subnets on the client side and two local subnets in the Cloud4U environment. Between the Edge Gateway in the cloud and Mikrotik at the client site, one IPsec tunnel will be established, and networks on each side will be routed through this tunnel.
Due to the fact that we cannot aggregate multiple networks into a single network with a shorter prefix, we will need to create a separate IPsec policy for each pair of networks. We will configure everything through the GUI of VMware Cloud Director and Winbox web interface.
The testing environment, on which we will perform the configuration, will look like this:
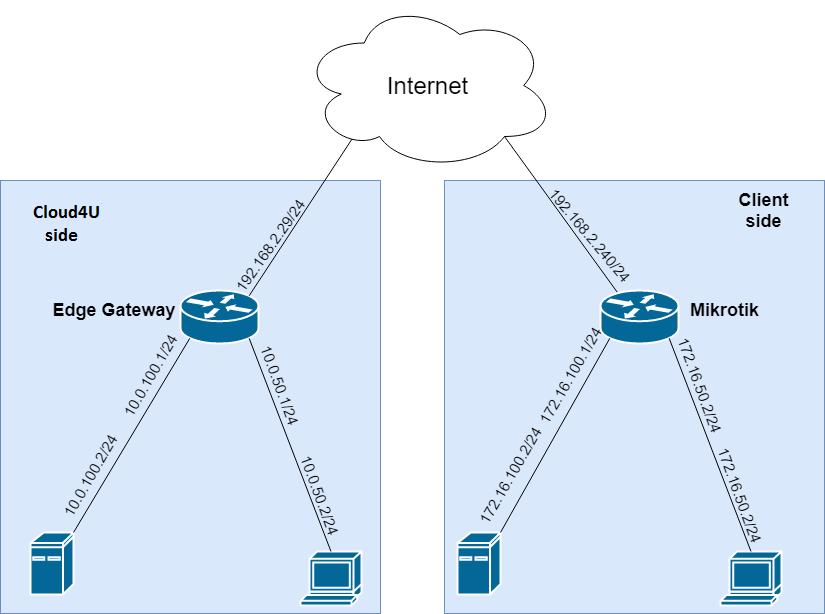
The network 192.168.2.0/24 is a laboratory network. For real-world use, globally routable (public, white-space) addresses on the internet will be used instead.
At Cloud4U, we have networks with the following CIDR ranges:
- 10.0.100.0/24
- 10.0.50.0/24
On the client side, we use the following networks:
- 172.16.100.0/24
- 172.16.50.0/24
We are running RouterOS version 6.48.1 on Mikrotik routers.
To configure the Edge Gateway, open the VMware Cloud Director control panel and navigate to the Networking section. Select the Edge Gateways tab and click on "Edge Gateway" to start configuring.
Choose Services
Configuring IPsec on Edge Gateway.
Go to VPN -> IPsec VPN -> IPsec VPN Sites click «+»

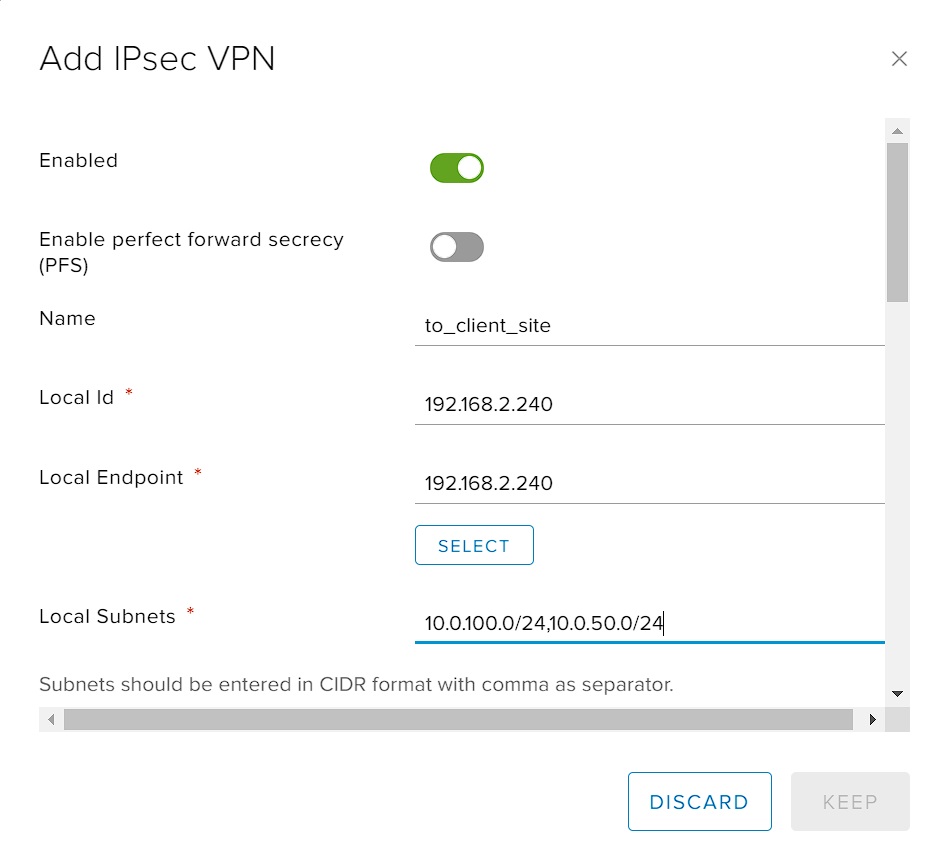
Enable IPsec VPN site, disable Perfect Forward Secrecy (PFS) because with this option enabled, tunnel crashes are observed. In order to avoid problems, we recommend disabling PFS.
In the "Name" field, enter the name of the IPsec tunnel.
In the "Local Id" field, enter a unique identifier. It can be an IP address or a domain name. The Local Id on the Edge Gateway must be the same as the Remote Id on Mikrotik.
In "Local Endpoint", enter the external IP address of Edge Gateway.
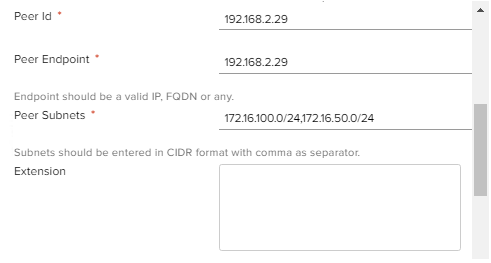
In "Local Subnets", enter a comma-separated list of subnets behind Edge Gateway that will be accessible through this tunnel.
Fill in the fields Peer Id, Peer Endpoint, Peer Subnets like Local. Specify the Id, the external IP address of the Mikrotik and the network behind the Mikrotik.
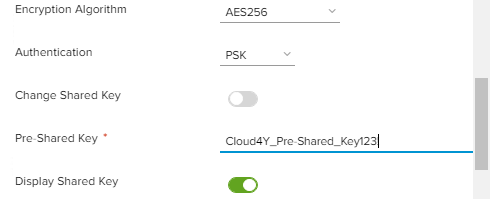
Choose the AES256 encryption algorithm, the PSK authentication method, and specify the Pre-Shared Key.
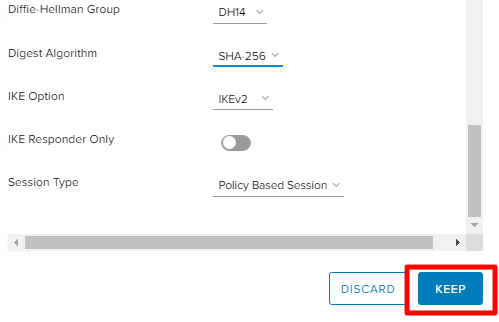
Repeat the settings from the screenshot and click Keep.
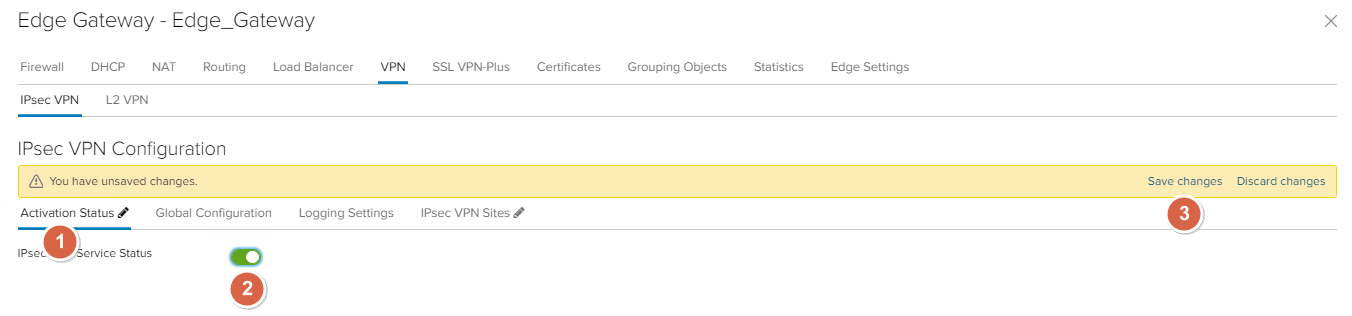
Go to the Activation Status tab, enable the IPsec Service and save changes.
Configuring Firewall on Edge Gateway
To ensure that traffic is not blocked by the Firewall, create rules. In the example below, create rules that allow all outgoing traffic and all traffic over the IPsec tunnel.
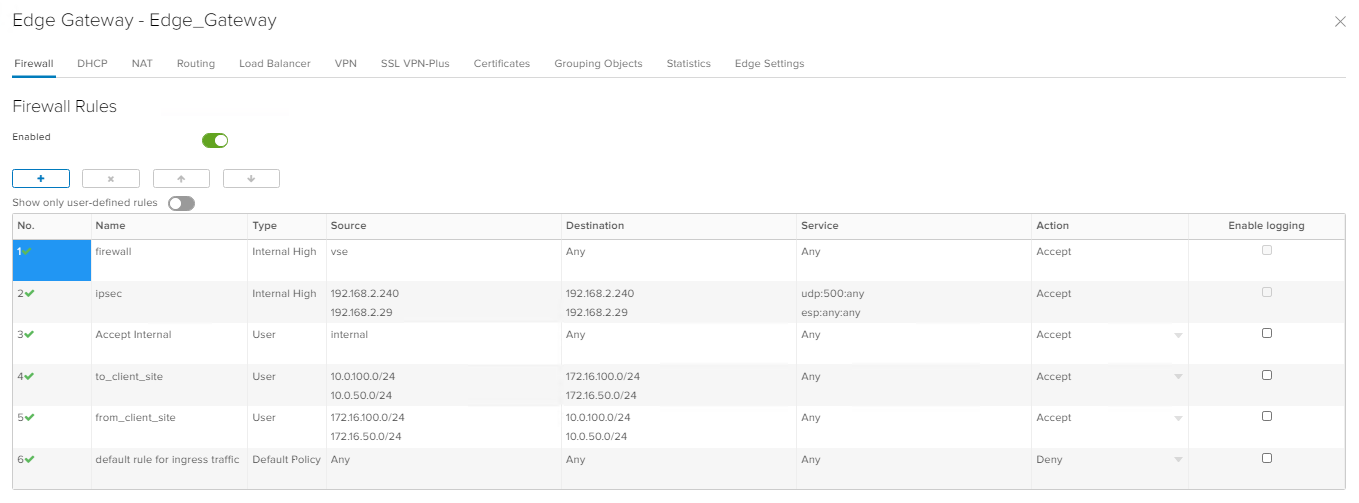
Edge Gateway configuration is complete.
Configuring Mikrotik
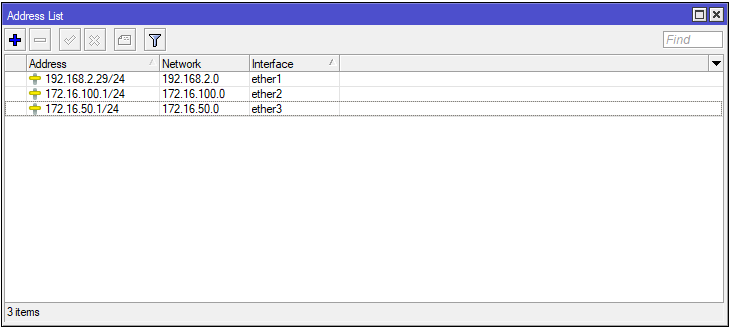
The instructions assume that the basic Mikrotik configuration has already been done. The following addresses are assigned to the Mikrotik interfaces:
Configuring IPsec on Mikrotik
Go to IP -> IPsec -> Peers «+».
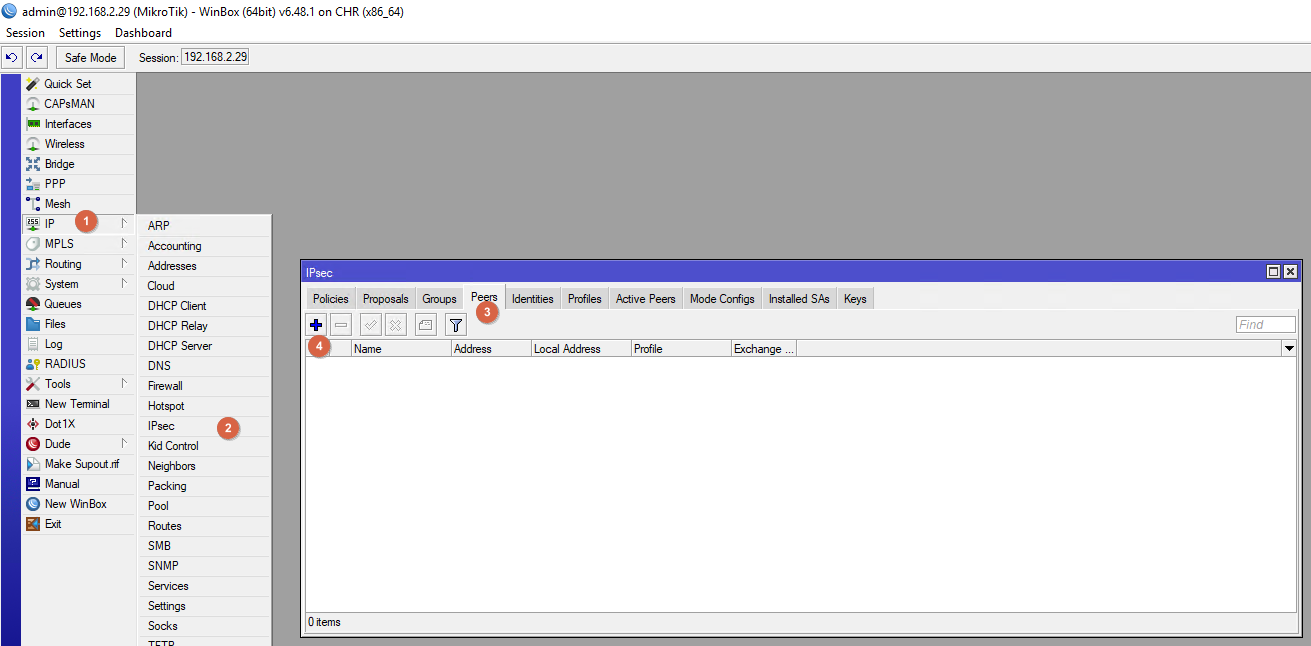
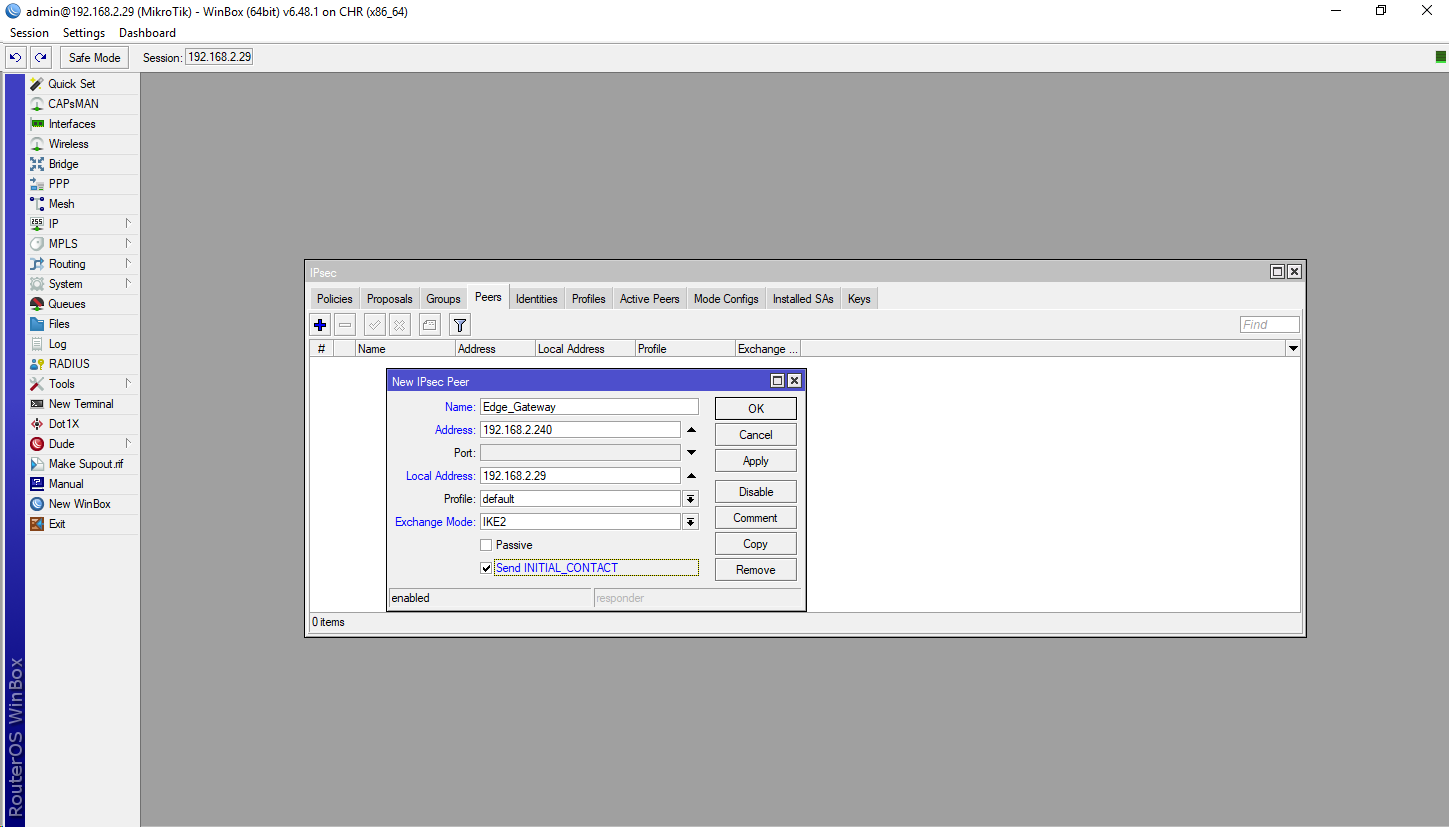
Create a new IPsec Peer.
In Address, enter the external IP address of the Edge Gateway.
In Local Address, put the external IP address of the Mikrotik.
Exchange Mode - IKE2.
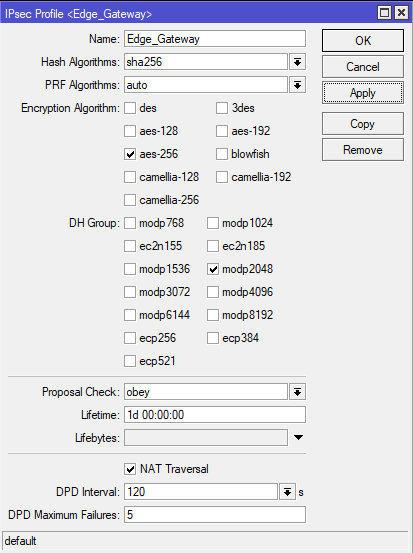
Go to Profiles. Edit the existing default profile.
Follow the settings from the screenshot.
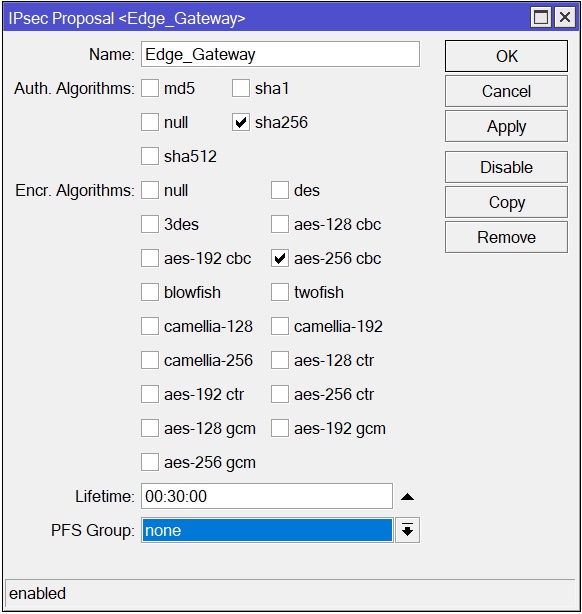
Go to Proposals. Create a new IPsec Proposal.
Repeat the parameters from the screenshot.
Go to Identities. Create a new Identity.
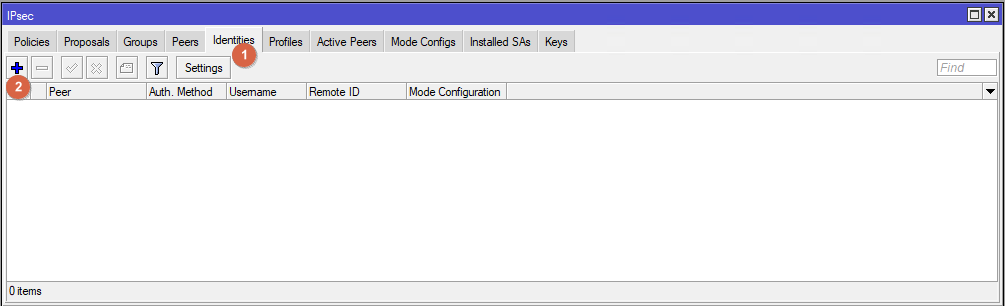
Repeat the settings from the screenshot. In the Secret field enter Pre-Shared key. The same as we entered when configuring Edge Gateway.
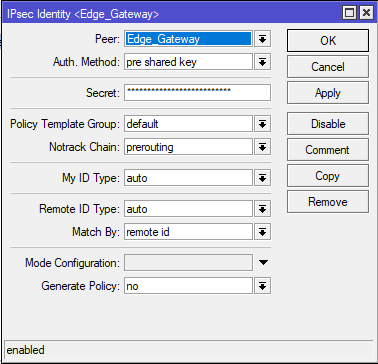
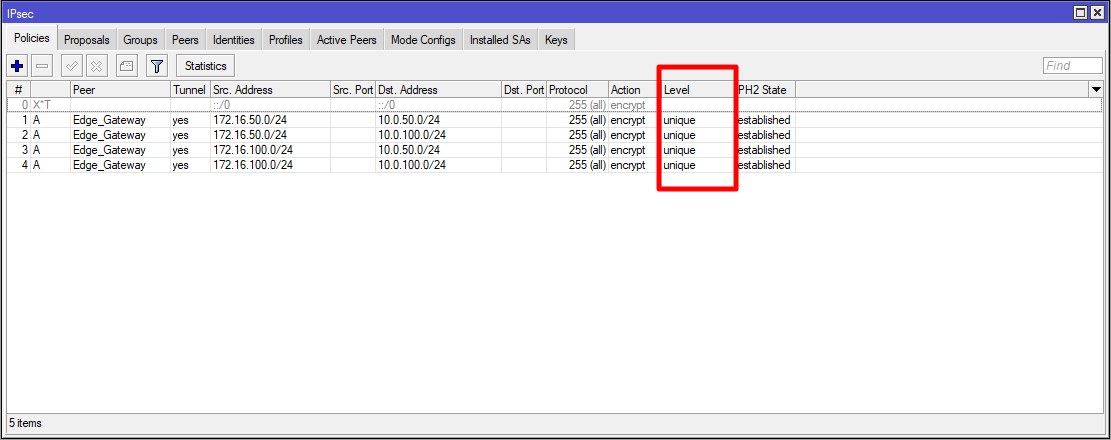
Go to Policies and create four IPsec Policy.
Create policies for each pair of networks.
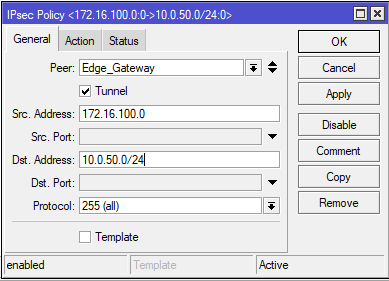
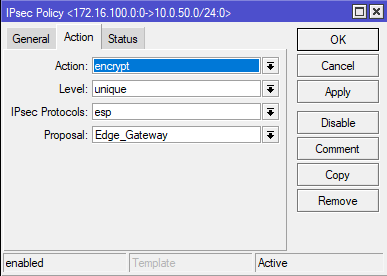
Correctly created policies should look like this. Pay attention to the "Level" column, the value next to each policy should be "Unique".
Configuring Firewall on Mikrotik
Go to IP -> Firewall -> Address Lists.
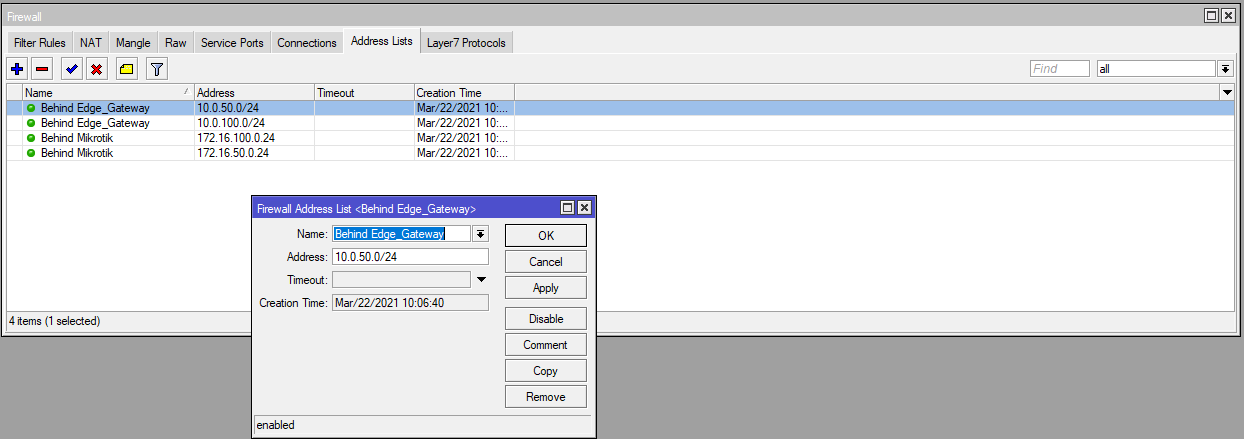
Create the address lists "Behind Mikrotik" and "Behind Edge_Gateway".
Specify which subnet is behind which router.
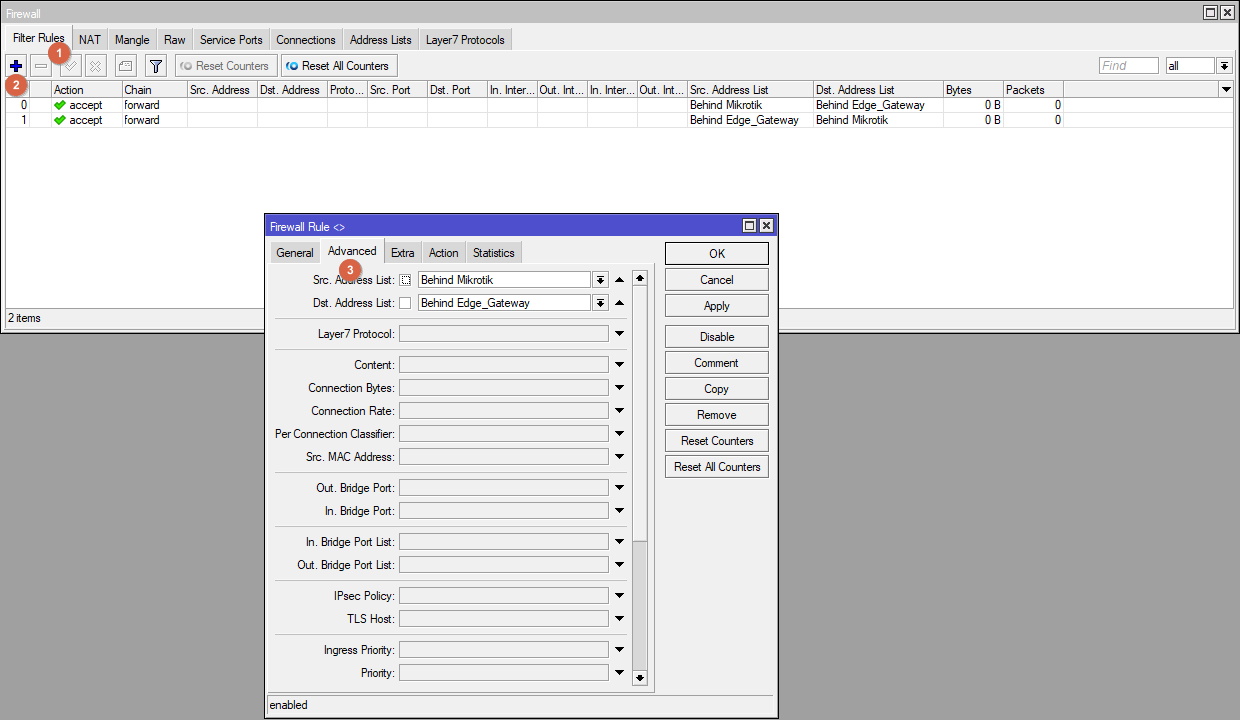
Create two "mirror" Firewall rules. On the Advanced tab select the address sheets created in the previous step.
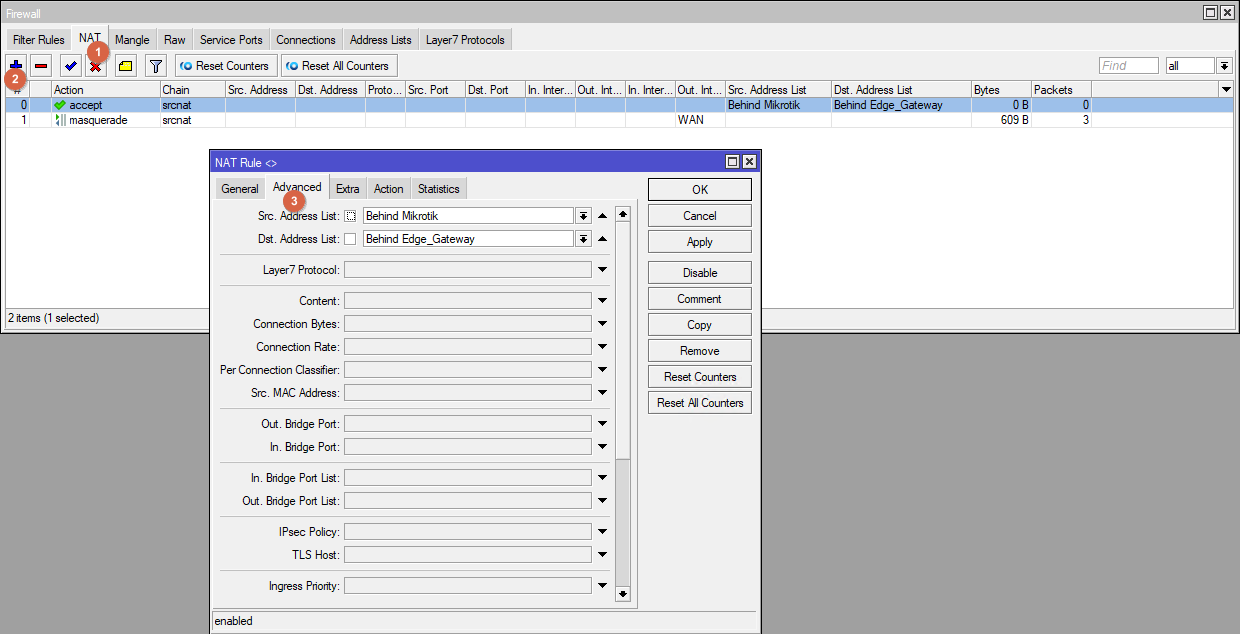
Create two "mirror" NAT rules. On the Advanced tab select the address sheets. These rules must be higher in the list than the Masquerade rule.
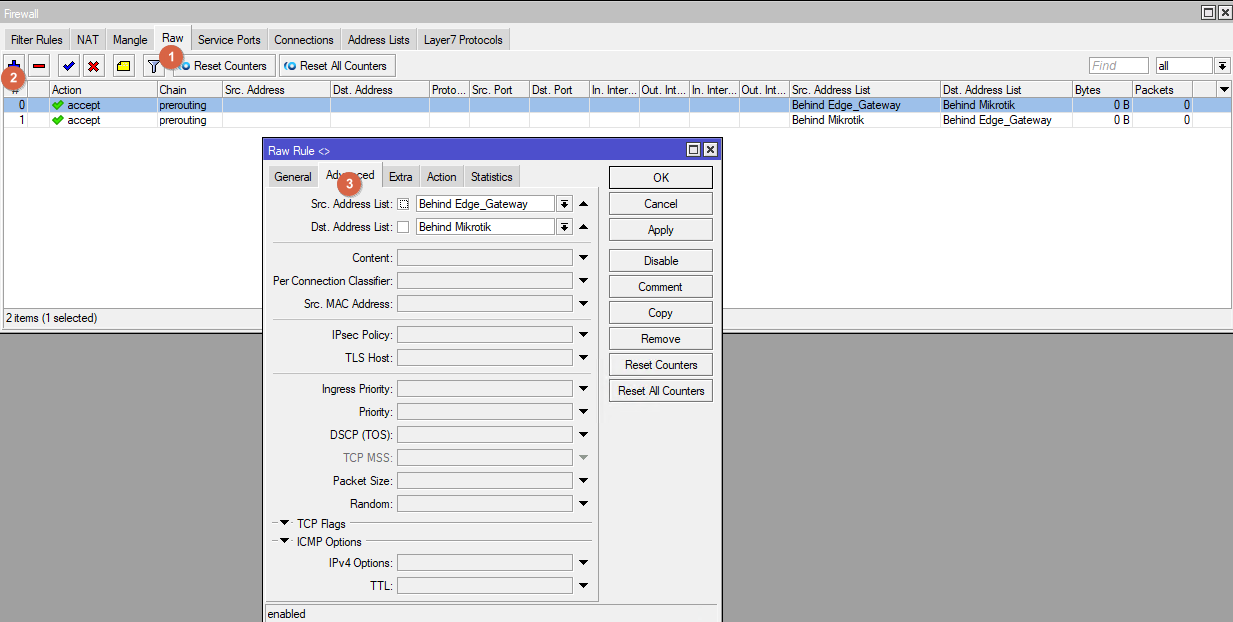
Create two "mirror" RAW rules. On the Advanced tab, select the sheet address.
Mikrotik configuration is complete.
