Getting Started
This tutorial shows how to receive, modify and send XML blocks representing the configuration of IPsec VPN tunnels within an EDGE gateway. The guide covers changing local and peer IP addresses, local and peer IDs, and adding or removing local and peer subnets.
Use Scenarios:
- Allows clients to quickly make changes to IPsec configurations
- Changes of this nature are not possible in the VMware Cloud Director GUI without first completely removing the existing IPsec VPN configuration and re-entering the settings. Depending on the number of tunnels, this can be a time-consuming task. Making changes to the IPsec VPN configuration using the vCloud API can significantly speed up this process.
Before you start
Before you get started
Before using the vCloud API to view and update your IPsec VPN settings, we recommend that you install a REST client that allows you to access the API. The steps in this article use the POSTMAN client, but you can also use the Firefox RESTClient plugin. For information on how to install this plugin and obtain the authorisation token and VDC credentials, see How to access VMware Cloud Director through the vCloud API. This guide does not cover the initial setup of the client.
Get vOrg information via the API
- Get an authorization token (See KB article)
- Create a GET request via API
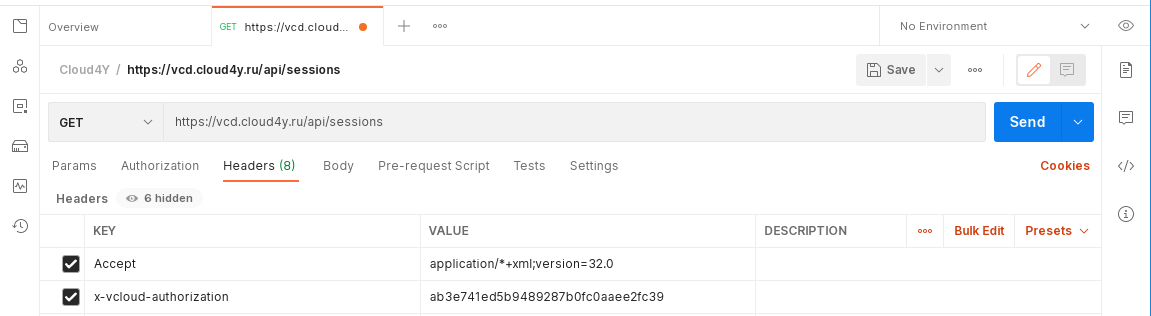
- In the server response, find the API URL to access vOrg
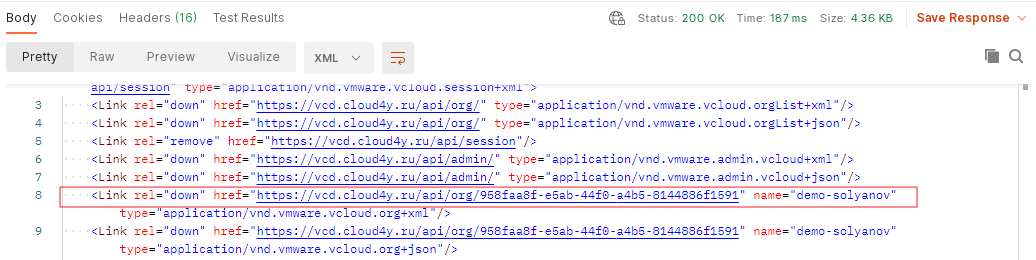
The resulting URL should look like this:
https://<api_url>/api/org/<org_id>
https://vcd.cloud4y.ru/api/org/958faa8f-e5ab-44f0-a4b5-8144886f1591
- Once we have a link to our organization, make a GET request to get the API URL about entities such as Networks, VDCs and directories belonging to vOrg. Here we will be interested in the API link to the VDC.
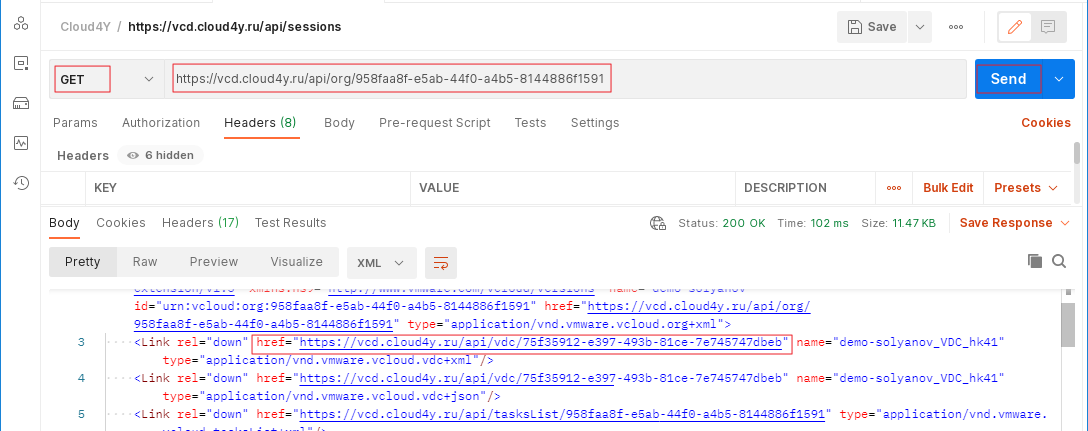
Obtaining VDC and EDGE information via AP
To obtain VDC unit information, follow these steps
1. Paste the received link into the query line and send the query
https://<api_url>/api/vdc/<vdc_id>
https://vcd.cloud4y.ru/api/vdc/75f35912-e397-493b-81ce-7e745747dbeb
- a new server response will be displayed, where we can find the API URL for the EDGE request

- Enter the specified URL in the query line to retrieve information about the specified EDGE. If the request was successful, the server should return a response where you can find the API URL of the EDGE you are interested in.
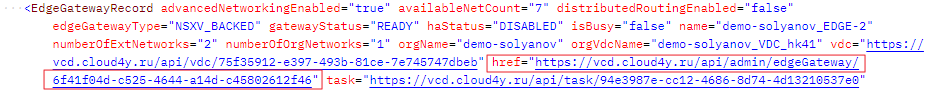
- Enter the API URL you found in the request line and make a GET request. If the response is successful, you will receive a server response with the following information
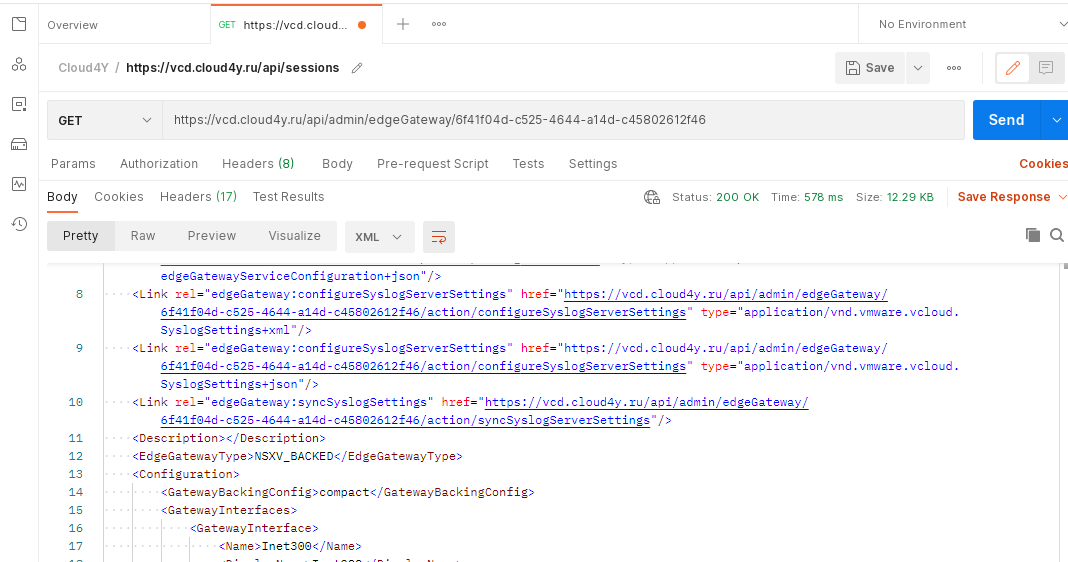
Checking the EDGE configuration
The output XML response contains EDGE configuration information between the opening <Configuration> and closing </Configuration> tags.
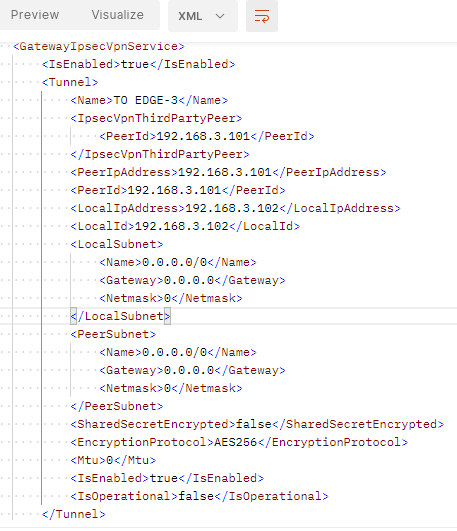
This XML block is divided into sections that detail the configuration parameters that apply to a particular item, feature or service available on the EDGE. There are twelve sections in total. However, we are only interested in the configuration parameters contained within the <GatewayIpsecVpnService> tags. The example below gives a general overview of the structure of the returned XML block, including the <GatewayIpsecVpnServices> tags.
! We recommend that you save the XML data from the <Configuration> tag to the <\Configuration> tag in a separate file. This is necessary to be able to roll back to a working version in case of incorrect changes.
Configuring the IPsec VPN settings in the returned XML
To edit the IPsec VPN settings, paste the content between the opening <GatewayIpsecVpnService> and closing </GatewayIpsecVpnService> tags into the text file. The content should look like the block of XML shown in the paragraph above.
You can now modify any of the parameters in this block.
The local IP address and local identifier are specified by the <localIpAddress> and </localIpAddress> tags, and the <localId> and </localId> tags respectively.
A remote tunnel endpoint to a new device or IP address, using the <PeerIpAddress> and <PeerId> tags (note that these values must match).
Local subnets using the <LocalSubnet> tag or remote local subnets using the <PeerSubnet> tag.
Shared secret changes the value between the opening <SharedSecret> and closing </SharedSecret> tags.
These changes are the most common when configuring IPSec tunnels.
Applying the new configuration
Once you have made changes to the xml data, you can apply them to the EDGE settings. To do this, fulfil the following conditions:
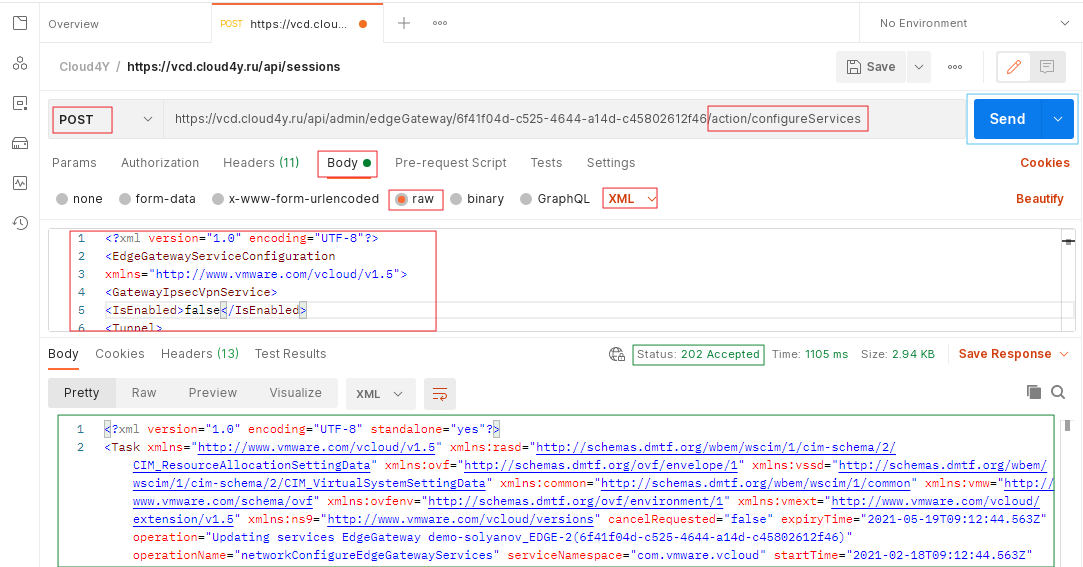
1. Close the new configuration with a pair of <EdgeGatewayServiceConfiguration> tags.
2. Copy and paste this configuration into the body section of the Postman client. In the settings of the window, specify the RAW data type, XML method.
3. In the list of request types, select POST.
4. In the URL address field, add the following to the URL /action/configureServices
5. Also make sure you have another header in Postman before sending the new configuration. Select Headers from the Headers menu at the top of the REST client.
6. Enter Content-Type in the Name field and the following in the Attribute Value field
application/vnd.vmware.admin.edgeGatewayServiceConfiguration+xml
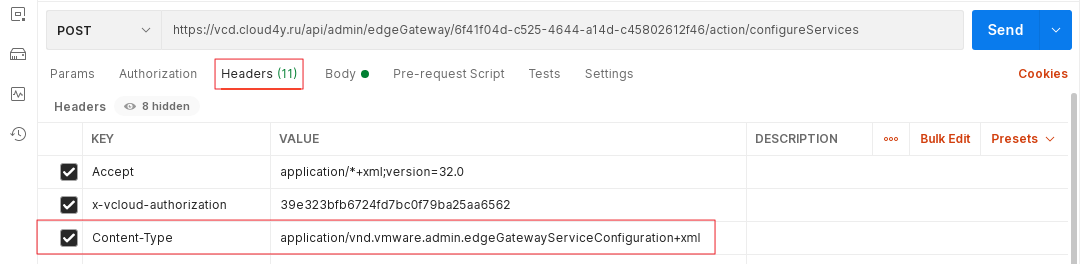
- Press Send to apply the new configuration.